The year 2020 is insane enough even without HIPAA fines. However, a gastroenterological practice from Utah still had to settle with the government for 100.000 dollars over a breach. While the violation is not as massive as, for example, in the AMCA case (the company had to file for bankruptcy), getting fined is still not the most pleasant way to spend your hard-earned money. In this article, we will give you some pointers on how to stay safe.
HIPAA fines size
As of the time this article is published, there are four levels of violations and the corresponding fines.
- “Didn’t know”. If the company didn’t know it had violated HIPAA and couldn’t possibly have known “by exercising reasonable diligence”, it could face from USD 100 to USD 50.000 for each individual violation.
- “Reasonable cause”. If there was a valid reason for noncompliance and there are no signs that the company neglected its HIPAA duties, the fines are from USD 1000 to USD 50.000.
- “Fixed in time”. If the company violated HIPAA due to willful neglect, but the issue “was timely corrected”, the fines are from USD 10.000 to USD 50.000″.
- “The worst case”. If the violation happened due to willful neglect and wasn’t corrected in time, the fine for a single violation is USD 50.000.
There are two main caveats to it.
The first one is the cap for the fines. A company can’t be fined more than USD 1.5 million for all the violations of each specific HIPAA requirement.
The second is that the fines are periodically adjusted for inflation using the abovementioned numbers as a baseline. Currently, the largest fine per single violation is USD 59,522, and the cap for all the violations of each requirement is USD 1,785,651.
Technical measures
Let us warn you in advance: information security is a huge topic. There is no way all the effective methods can be listed, let alone described, within a single article. Treat this as a set of pointers and guidelines, and contact us for a consultation if you need help.
There are two kinds of measures you can take: the required ones are obligatory, the addressable ones are used if they are necessary and reasonable.
Deidentification
This means storing health information in a way that makes it nigh-impossible to attribute to a specific individual. Deidentification can be done in two ways outlined in the HIPAA itself:
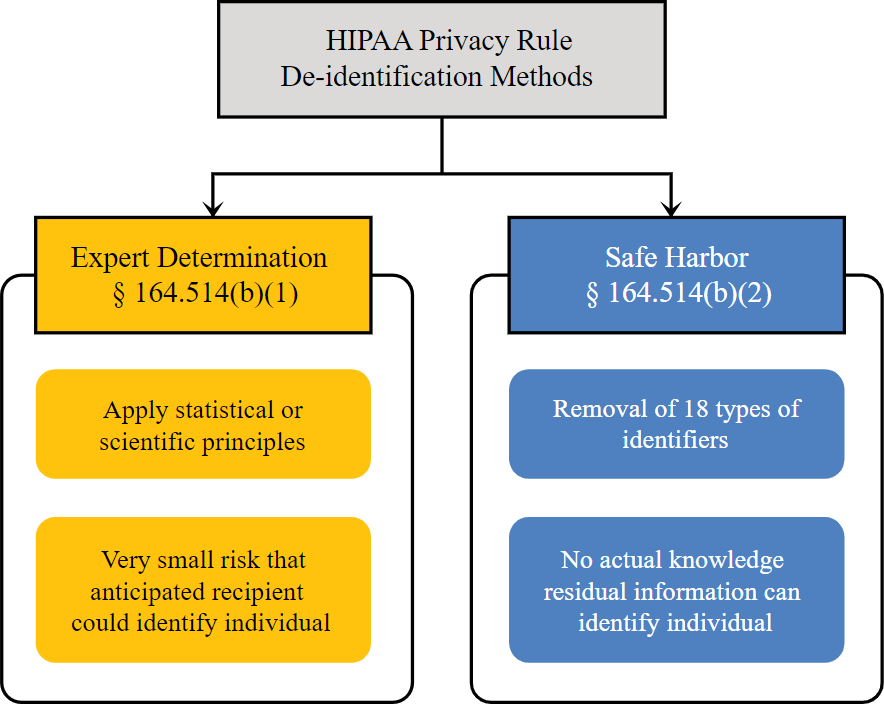
The first one is “expert determination”. If a sufficiently credible and knowledgeable person states that your method of information storage is safe enough and documents it, it is enough.
The second is called “safe harbor”. If you remove the 18 identifiers (name, address, device serial numbers, vehicle license plates, etc.) from your data it would be considered deidentified.
See more here.
Access Control
This HIPAA requirement states that the users need to have only the minimum information required to do their job.
For that, you will need a role-based access model where every position in the company has different levels of access to different data (e.g. a dental technician doesn’t get the ob-gyn information of a patient but has their complete dental profile).
Unique user identification
Each employee must have a unique ID. It can be either something simple (e.g. John Doe will have a login “jdoe”) or a random string of symbols that is harder to remember but is more secure.
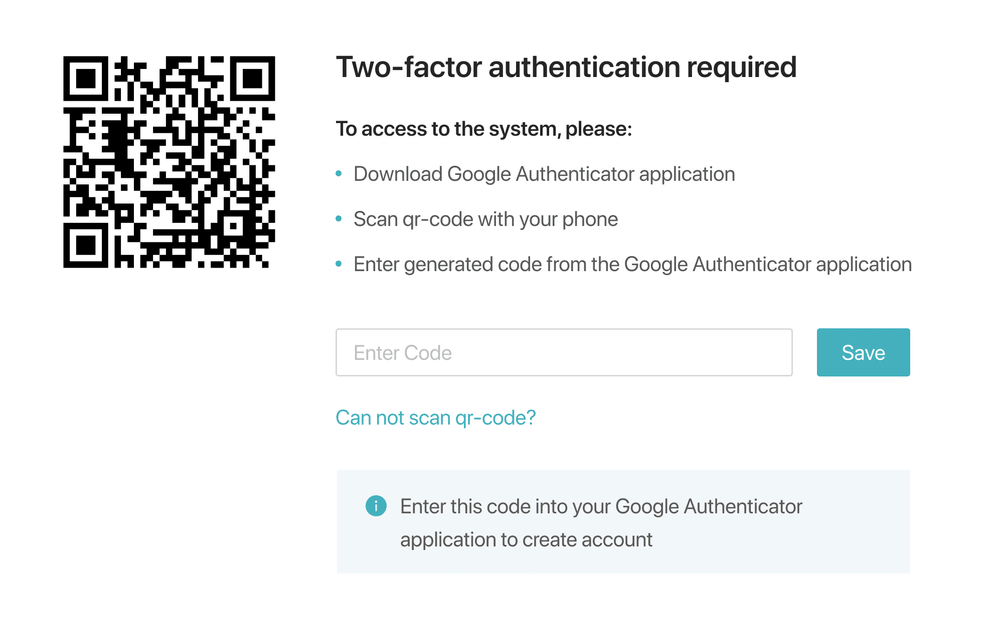
Emergency Access Procedure
The requirement states that in case of a force majeure, your records must still be accessible somehow. Possible ways of addressing this privacy issue include an on-premise double of your cloud-based records (or vice-versa), paper records, etc. The procedure should include access to both the medical and the billing functions of your software.
Automatic Log-Off
This is an addressable issue.
If an employee leaves their workstation without exiting the system, someone can take the opportunity and access confidential data. So to keep in line with the law it is recommended to set a 10-15 minute inactivity period after which the system logs the user off automatically.
Data Encryption
This is an addressable issue.
Even if the information is stolen, the malicious actor wouldn’t be able to use it when it is thoroughly encrypted.
There are many encryption methods that differ in their complexity and speed. But for all of them, you should store the keys outside of your system.
Audit Controls
Any activity related to electronic protected health information (ePHI) needs to be logged and monitored. This can be done by hardware and software means, but there should also be procedures that state how exactly the monitoring should work.
Data Integrity
This HIPAA requirement addresses the protection of data from unwanted changes or destruction. They can come either as a result of a user’s mistake (e.g. accidentally deleting a patient’s record) or someone’s malicious actions.
Either way, a good practice is to make regular backups of the information and store it on an external server.
It is an addressable measure.
Authentication
Authentication means making sure that the person accessing information is who they claim to be. It can be done by:
- Login/Password
- Biometrics (fingerprints, voice, etc.)
- Physical key
Multifactor identification (e.g. password + code in SMS) is also quite popular.
Integrity Controls
This HIPAA requirement includes any measures taken to protect data from being altered in transfer. Typically it is achieved by using encryption, e.g. SSL certificates.
Physical measures
These include data protection steps you need to take in the real world.
Contingency Operations
Just like with the system itself, people should be able to access its physical components (e.g. servers) even in emergency situations. This is an addressable measure.
Facility Security Plan
Sometimes you don’t need to hack to steal data — stealing the servers with it works well enough. So if it is reasonable for your company, prepare a plan covering physical access to the data storage. This is an addressable measure.
Access Control and Validation
Make sure that, for example, the technician working in your server room is who he claims to be and has the skills to do the job. It is an addressable measure.
Maintenance Records
Keep a log (on paper or electronically) of all the repairs made to the physical components of the facility (doors, locks, windows, etc.). This is an addressable measure.
Workstation Security
Regulate the use of any workstation that can access the protected data. The list includes physical safeguards (e.g. covers), automatic logoff, and other measures.
Data Disposal
This addresses the safe deletion of data. Whenever a record needs to be destroyed, make sure it is deleted everywhere (including backups, removable storage devices, etc.).
Media Re-use
If you need to reuse (or sell) a hard drive, for example, make sure it doesn’t contain any ePHI.
Accountability
Keep track of company-owned storage devices and make a log of everyone using them. This is an addressable measure.
Data Backup
There are no hard HIPAA requirements that specify the backup procedure and storage location. But make sure you check other regulations (e.g. state laws) to be safe.
Administrative measures
These mostly include company policies that promote safe data handling. They include appointing a compliance officer, risk management, employee training, making a continuity of operations plan, etc.
Breach Notification
Besides notifying the affected individuals, if a HIPAA breach is discovered, you’ve got 60 days to report it to the Department of Health and Human Services. If it affects at least 500 people, you’ll also need to contact the media as well. This is what you should include in the notification:
- The nature of the ePHI involved, including the types of personal identifiers exposed.
- The unauthorized person who used the ePHI or to whom the disclosure was made (if known).
- Whether the ePHI was actually acquired or viewed (if known).
- The extent to which the risk of damage has been mitigated.
Conclusion
Hopefully, you now have an understanding of the basic measures your product or practice needs to be HIPAA compliant. If not — feel free to reach out to us. We can both give you a consultation (first one’s free!) and implement the necessary measures.